In an increasingly digital world, cybersecurity is no longer optional—it’s essential. For Australian organisations, the Australian Signals Directorate (ASD) Essential Eight provides a practical, prioritised framework to mitigate cyber threats. Developed by the Australian Cyber Security Centre (ACSC), the Essential Eight is designed to help organisations protect their systems against a wide range of cyber-attacks, particularly those involving ransomware and data breaches.
This is the Australian federal government’s recommendation for all businesses turning over $3M+/PA
What is the ASD Essential Eight?
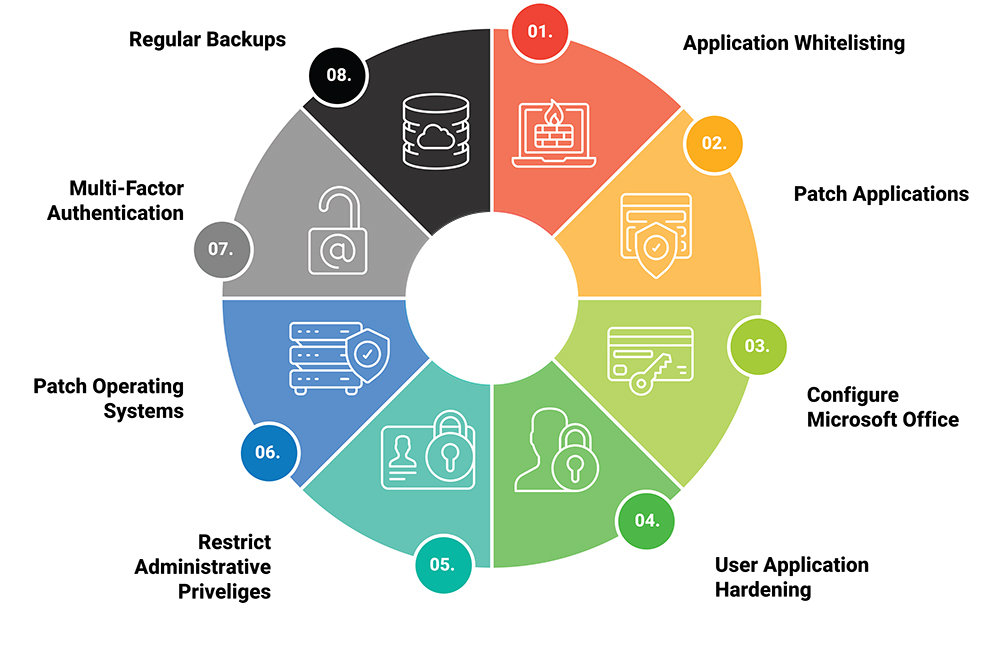
The Essential Eight is a set of baseline mitigation strategies that organisations can implement to improve their cybersecurity posture. These strategies are:

- Application Control – Preventing the execution of unapproved or malicious programs.
- Patch Applications – Regularly updating software to fix security vulnerabilities.
- Configure Microsoft Office Macro Settings – Restricting the use of macros to reduce the risk of malware.
- User Application Hardening – Disabling unnecessary features in applications to reduce attack surfaces.
- Restrict Administrative Privileges – Limiting access to systems and data based on user roles.
- Patch Operating Systems – Keeping OS software up to date to prevent exploitation.
- Multi-Factor Authentication (MFA) – Adding an extra layer of security beyond passwords.
- Regular Backups – Ensuring data can be restored in case of loss or ransomware attacks.
Why Is It Relevant to the Australian Market?
Australia has seen a sharp rise in cyber incidents, with high-profile breaches affecting both public and private sectors. The Essential Eight is particularly relevant because:
- Government Mandate: Federal and state agencies are increasingly required to align with the Essential Eight maturity model, making it a compliance necessity.
- Local Threat Landscape: Australian organisations face targeted attacks from both domestic and international actors. The Essential Eight addresses common vectors used in these attacks.
- Cost-Effective Security: The framework is designed to be achievable and scalable, making it suitable for SMEs as well as large enterprises.
- Risk Management: Implementing the Essential Eight helps organisations meet broader risk management and governance obligations under frameworks like ISO 27001 and the Australian Privacy Act.
Weaknesses and challenges in this framework
The ASD Essential Eight is a strong foundational cybersecurity framework, but like any model, it has limitations. Here are some of the key weaknesses and challenges associated with it, particularly in the context of the Australian market:
- Not Comprehensive for All Threats
- One-Size-Fits-All Approach
- Implementation Complexity
- Lack of Cloud and Mobile Focus
- Maturity Model Ambiguity
- Limited Integration with Broader Frameworks
Conclusion
The ASD Essential Eight is more than a checklist—it’s a strategic approach to cybersecurity that aligns with Australia’s national interests. As the name implies this is for ‘essential’ controls and remains a valuable starting point for cybersecurity in Australia. However, organisations should view it as part of a layered security strategy, not a complete solution. Tailoring controls to specific business needs, environments, and threat profiles is key to achieving true cyber resilience.